Reverse Engineering Tutorial
Here I will show you reverse engineer with Winrarusing Olly debugger. In this tutorial I will show you the attackers approach of simply hacking a software with just basic understanding of Assembly.
You will need Olly dbg(v 1.10) and Winrar
Our target is to bypass the registration screen that pops in-front of us everytime we load winrar. We have to prevent that screen from appearing without registering the software. So all we have to do is get rid of this Reminder.

POINT 1 - Run olly dbg and open winrar in it by dragging it and dropping it in olly dbg.
POINT 2 - You will find a screen similar to it. If you have read the previous two tutorials of this series thaen it will help you understand the things that will come in-front of you else everything will appear Greek. You will find something similar to this. Go through the whole code once.

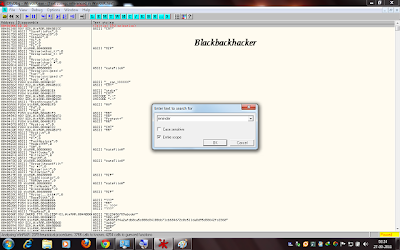
POINT 3 - Now right clcik on the CPU main thread module and go to Search For > All Referenced text String.
POINT 5 - Now again right click on this new window and click on Search for text.
POINT 7 - On pressing enter you will reach to the particular string location . You will see similar to the one shown in figure.
POINT 8 - Now double click it (reminder) and you will be taken to the main thread location of the string "reminder". Refer figure again. So now you have reached to the location that is responsible for generating the particular reminder message that pops up every-time we start winrar. Now from here you will need a basic understanding of Assembly.
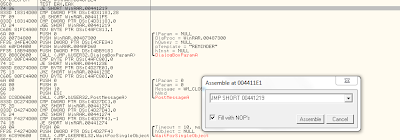
POINT 9 - Upon careful analysis of the region around the "reminder" text you will find a statement similar to this " JE SHORT winrar.00441219 " . If you remember the things we learned in our previous tutorial then "JE" means "jump if equals". This means that if your copy of winrar is already a registered copy then this statement will prevent the execution of the reminder message. So what shold we do here so that it still doesn't display the reminder even though we have an unregistered copy of winrar.
POINT 10 - Now go to the jump statement and double click it. Now change "JE SHORT winrar.00441219" to " JMP SHORT winrar.0041219 " . BUT WHY ? Find out the answer yourself. If the concept is clear then you already have the answer.
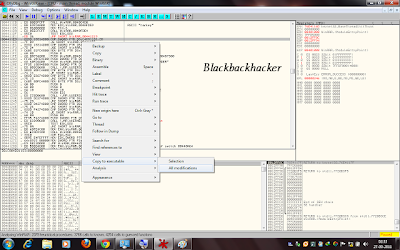
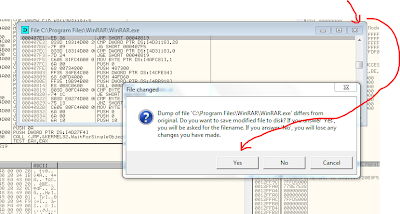
POINT 11 - Now you have to save changes to the executable to see if you have performed the RE process correctly or not. All you need to do now is go to the CPU main thread module , right click > copy to executable > all modifications. Press yes for the alert messages. You can either save it with the same name as winrar.exe to over-right the previous file or you can first save it with a different name to check if you have succeeded or not.




Very well written post. It will be beneficial to everyone who utilizes it, including me.
ReplyDeleteKeep doing what you are doing - looking forward to more posts.
Also visit my web-site: porno xxx 2011
Hi there, after reading this amazing paragraph i am also happy to share
ReplyDeletemy knowledge here with mates.
Have a look at my blog; infonews